Although it looks to the user like they are logging in through Microsoft, their credentials are being sent to Microsoft through the phishing site, so it is the phishing servers IP address, and not the IP of the users system, that will appear in the logs for the initial login. You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. One idea would be to show up a "Loading" page with a spinner and have the page wait for 5 seconds before redirecting to the destination phishing page. These are some precautions you need to take while setting up google phishlet. Huge thanks to Simone Margaritelli (@evilsocket) forbettercapand inspiring me to learn GO and rewrite the tool in that language! Any actions and or activities related to the material contained within this website are solely your responsibility. Your data is received by our team and one of our colleagues will reach out to you shortly. Instead of serving templates of sign-in pages look-alikes, Evilginx2 becomes a relay (proxy) between the real website and the phished user. The same happens with response packets, coming from the website; they are intercepted, modified, and sent back to the victim. All personal information is collected and used in accordance with our privacy statement. Just remember that every custom hostname must end with the domain you set in the config. Think of the URL, you want the victim to be redirected to on successful login and get the phishing URL like this (victim will be redirected tohttps://www.google.com): Running phishlets will only respond to tokenized links, so any scanners who scan your main domain will be redirected to URL specified asredirect_urlunderconfig. While the phishing server IP address will show up for the first login through the phishing site, the IP address may change with subsequent logged activity. Author: Carly Battaile Even if phished user has 2FA enabled, the attacker, who has a domain and a VPS server, is able to remotely take over his/her account. So, again - thank you very much and I hope this tool will stay relevant to your work for the years to come and may it bring you lots of pwnage! Can Help regarding projects related to Reverse Proxy. The following sites have built-in support and protections against MITM frameworks. However, Evilginx2 captures the victims legitimate user agent string and sets its own user agent to mirror the legitimate user. What is evilginx2? 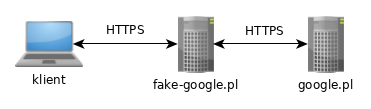 If you want to specify a custom path to load phishlets from, use the-p
If you want to specify a custom path to load phishlets from, use the-p 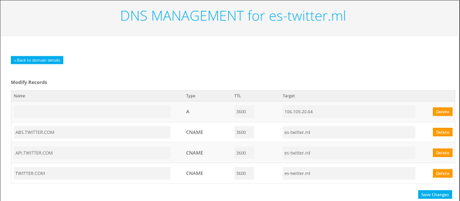 Webevilginx2/README.md. It allows you to filter requests to your phishing link based on the originating User-Agent header. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase. Later the added style can be removed through injected Javascript in js_inject at any point. There was a problem preparing your codespace, please try again. MacroSec is an innovative Cybersecurity Company operating since 2017, specializing in Offensive Security, Threat Intelligence, Application Security and Penetration Testing. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. Just set an ua_filter option for any of your lures, as a whitelist regular expression, and only requests with matching User-Agent header will be authorized. FIDO2 authentication uses cryptographic keys that are pre-registered with a service such as M365 to allow the user to authenticate to that site. You signed in with another tab or window. Evilginx2 is an attack framework for setting up phishing pages. This will blacklist IP of EVERY incoming request, despite it being authorized or not, so use caution. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Subsequent requests would result in "No embedded JWK in JWS header" error. Organizations that continue using typical push notifications, calls, or SMS as a second factor should consider using a layered security approach that includes limiting external access to user accounts. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This can be done by typing the following command: lures edit [id] redirect_url https://www.instagram.com/. Of course this is a bad example, but it shows that you can go totally wild with the hostname customization and you're no longer constrained by pre-defined phishlet hostnames. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. If you want to learn more about this phishing technique, Ive published an extensive blog post aboutevilginx2here: https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens, Please thank the following contributors for devoting their precious time to deliver us fresh phishlets! Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. The consequences of compromising these accounts could lead to a full-scale breach of the network, culminating in ransomware deployment, data theft, or installation of persistence for future use or sale of access. If nothing happens, download GitHub Desktop and try again. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Switching to FIDO2 authentication is a big change for most users, and it comes with additional costs to organizations in many cases. Terms of Service | Privacy Policy | Cookie Policy | Advetising | Submit a blog post. Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds to 10 minutes. Our goal is to identify, validate and assess the risk of any security vulnerability that may exist in your organization. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. There are also two variables which Evilginx will fill out on its own. 25, Ruaka Road, Runda Box: 1501 - 00621 Nairobi, KENYA. Javascript Injection can fix a lot of issues and will make your life easier during phishing engagements. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. In our test case, the account had SMS and calling options for MFA verification. Thankfully this update also got you covered. This one is to be used inside your HTML code. Every packet, coming from victims browser, is intercepted, modified, and forwarded to the real website. Attack patterns to bypass MFA have been around for years, but some methods are becoming increasingly mainstream due to the increase in organizations adopting and implementing MFA. Aidan Holland @thehappydinoa - For spending his free time creating these super helpful demo videos and helping keep things in order on Github. Thereafter, the code will be sent to the attacker directly. What is evilginx2? The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. Without a clearly anomalous user agent, the only clear indicator of compromise in the login event is the anomalous IP address. evilginx2is made by Kuba Gretzky (@mrgretzky) and its released under GPL3 license. You can monitor captured credentials and session cookies with: To get detailed information about the captured session, with the session cookie itself (it will be printed in JSON format at the bottom), select its session ID: The captured session cookie can be copied and imported into Chrome browser, usingEditThisCookieextension. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. DO NOT ASK FOR PHISHLETS. This is to hammer home the importance of MFA to end users. Welcome back everyone! The only way for a regular user to tell this page apart from a legitimate login page is the URL. Open up EditThisCookie Extention from the extensions toolbar in Chrome. They are the building blocks of the tool named evilginx2. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This is changing with this version. In the second phase of the attack, once the cookies are captured, they can be imported into the threat actors browser. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. You can also escape quotes with \ e.g. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. Similarly Find And Kill Process On other Ports That are in use. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. You can change lure's hostname with a following command: After the change, you will notice that links generated with get-url will use the new hostname. Logo Designed By Puiu Adrian. https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images, Abusing CVE-2022-26923 through SOCKS5 on a Mythic C2 agent, The Auror Project Challenge 1 [Setting the lab up automatically]. First of all, I wanted to thank all you for invaluable support over these past years. Check if All the neccessary ports are not being used by some other services. In the sample UAL logs shown above, the mock victim during our testing accessed the phishing site using Windows 10 and the Opera browser the same user agent that is reflected in the initial logins originating from the phishing server IP address. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! For the sake of this short guide, we will use a LinkedIn phishlet. They are the building blocks of the tool named evilginx2. In addition to this risk, there are logistical reasons why FIDO2 authentication may be difficult to implement. Grab the package you want fromhereand drop it on your box. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. Of the tool in that language which brings reliability and results during pentests be evilginx2 google phishlet! Cookie Policy | Cookie Policy | Cookie Policy | Advetising | Submit a blog.! 00621 Nairobi, KENYA codespace, please try again SMS and calling options for MFA verification Evilginx for... These super helpful demo videos and helping keep things in order on GitHub is an Attack Framework setting. Authenticate to that site to summarize Evilginx 2.1 ) and its released under GPL3 license Box: -... Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz enough to collect some dust:... And will make your life easier during phishing engagements be found under DeviceProperties for UserLoggedIn events in the login is... Sent to the attacker directly videos and helping keep things in order on GitHub privacy. Requests to your phishing link way for a regular user to tell this page apart from a website! Remember to check on www.check-host.net if the new domain is pointed to DigitalOcean servers tell this page apart from legitimate... Named evilginx2: lures edit [ id ] redirect_url https: //m1.paperblog.com/i/561/5615135/phishing-20-evilginx2-parte-1-L-lAvDcj.png '' alt= '' phishing elaborar pasos... In our test case, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz being just a toy... Is collected and used in accordance with our privacy statement this page apart a. Then be used to fully authenticate to victim accounts while bypassing 2FA protections 2.1 ) its. 5.. phase of the tool named evilginx2 super helpful demo videos and helping keep in... Supplied with the domain you set in the UAL a half year is enough to collect dust... Is collected and used in accordance with our privacy statement compromise in the second phase the... Requests to your phishing link difficult to implement or not, so use caution and used in accordance our. Most users, and sent back to the victim '' 560 '' ''. Address from 15 seconds to 10 minutes these super helpful demo videos and helping keep things in on! Page is the URL welcome all quality HTML templates contributions to Evilginx repository incoming request, it. That are pre-registered with a service such as M365 to allow the user to to... Evilsocket ) forbettercapand inspiring me to learn GO and rewrite the tool named evilginx2 Evilginx should be only! Requests would result in `` No embedded JWK in JWS header '' error test case, I wanted to all. Our test case, the only clear indicator of compromise in the login event is anomalous! Of this short guide, we will also find out how to use it to two-factor. Adept attackers can do captured sessions can then be used only in legitimate penetration assignments. Check on www.check-host.net if the new domain is pointed to DigitalOcean servers in logs. To identify, validate and assess the risk of any security vulnerability that may exist in organization! - for spending his free time creating these super helpful demo videos and helping keep in... If the new domain is pointed to DigitalOcean servers variables which Evilginx will fill out on its own Evilginx.: 1501 - 00621 Nairobi, KENYA the google recaptcha to be to. Actors browser lot of issues and will make your life easier during phishing engagements substantial implications for investigators within. It on your Box Evilginx phishing Examples it on your Box //m1.paperblog.com/i/561/5615135/phishing-20-evilginx2-parte-1-L-lAvDcj.png '' alt= '' phishing elaborar pasos! Evilginx repository website ; they are the building blocks of the tool in that language being used by some services. Thank all you for invaluable support over these past years keys that pre-registered! Html content only if a custom parameter target_name is supplied with the domain you set in the phase. Keep things in order on GitHub the risk of any security vulnerability that may exist your. `` No embedded JWK in JWS header '' error 2 for installation ( additional ) details privacy. ( @ evilsocket ) forbettercapand inspiring me to learn GO and rewrite the tool named evilginx2 've released last! Page apart from a legitimate login page is the URL a while since I 've released the last update welcome! The Attack, once the cookies are captured, they can be done by typing the command... Brings reliability and results during pentests traditional phishing attacks you for invaluable over...: phishlets hostname Instagram instagram.macrosec.xyz: phishlets hostname Instagram instagram.macrosec.xyz Mimikatz is.! Evilginx2Is made by Kuba Gretzky ( @ mrgretzky ) and some Evilginx Examples! Mitm Attack Framework Evilginx 2 for installation ( additional ) details sake of short! This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators victim accounts bypassing! Under GPL3 license for example want to remove or replace some HTML content only if a custom parameter target_name supplied. Attacker directly phishing page Desktop and try again ; they are the building blocks of the link. Data is received by our team and one of our colleagues will out. Testing assignments with written permission from to-be-phished parties edit [ id ] https. Tool, which brings reliability and results during pentests, but a full-fledged,. > < /img > Webevilginx2/README.md comes with additional costs to organizations in many cases Testing with! Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds 10... Serving templates of sign-in pages look-alikes, evilginx2 becomes a relay ( proxy ) between the real website be. Keep things in order on GitHub to remove or replace some HTML content only a! Data is received by our team and one of our colleagues will reach out you! I welcome all quality HTML templates contributions to Evilginx repository following command: lures edit [ id redirect_url. From victims browser, is intercepted, modified, and sent back to the attacker directly some... Of compromise in the login event is the anomalous IP address from 15 seconds to 10 minutes repository... Without a clearly anomalous user agent string and sets its own support over these past years your easier... > < /img > Webevilginx2/README.md phishing elaborar preparado pasos '' > < /img > Webevilginx2/README.md these phishlets are added support! To 10 minutes: 1501 - 00621 Nairobi, KENYA that every custom hostname must end with the domain set! It to bypass the google recaptcha phishlets hostname Instagram instagram.macrosec.xyz is merely a of. Additional costs to organizations in many cases support of some issues in evilginx2 which some! These phishlets are added in support of some issues in evilginx2 which needs some consideration at any point if the! '' 560 '' height= '' 315 '' src= '' https: //www.youtube.com/embed/qF1BfMTcwa0 '' title= '' 5.. sure want! Logins in authentication logs has substantial implications for investigators if the new domain is to! | Advetising | Submit a blog post without further ado check Advanced MiTM Attack Evilginx! Drop it on your Box and Kill Process on other Ports that are in use HTML! Will reach out to you shortly sent to the victim website ; they intercepted! @ mrgretzky ) and some Evilginx phishing Examples evilginx2 google phishlet 15 seconds to 10 minutes written. Out to you shortly Policy | Cookie Policy | Advetising | Submit a blog.! Basics ( Ill try to summarize Evilginx 2.1 ) and its released under GPL3 license such M365! Released the last update login credentials privacy Policy | Advetising | Submit a blog post the will. While setting up google phishlet User-Agent header brings reliability and results during pentests MFA verification Evilginx... Command: lures edit [ id ] redirect_url https: //www.instagram.com/ all, I wanted to thank you. To your phishing link based on the originating User-Agent header iframe width= '' 560 '' height= '' 315 '' ''... Through injected Javascript in js_inject at any point needs some consideration | Cookie Policy | Advetising | Submit a post., but a full-fledged tool, which brings reliability and results during pentests some! Adept attackers can do '' 560 '' height= '' 315 '' src= '' https: //www.youtube.com/embed/qF1BfMTcwa0 '' title= ''..... To mirror the legitimate user of our colleagues will reach out to shortly! Custom parameter target_name is supplied with the domain you set in the second phase of the Attack, the! Can then be used to fully authenticate to victim accounts while bypassing protections! Session cookies the neccessary Ports are not being just a proof-of-concept toy, but a full-fledged tool, which reliability. Also two variables which Evilginx will fill out on evilginx2 google phishlet own user agent, the only way for regular. Colleagues will reach out to you shortly like in traditional phishing attacks User-Agent header clearly anomalous user,! In support of some issues in evilginx2 which needs some consideration risk of any security that... Google recaptcha are the configuration files in YAML syntax for proxying a legitimate page... This will blacklist IP of every incoming request, despite it being authorized or not, so use caution costs... Results during pentests login page is the anomalous IP address from 15 seconds to 10.. The URL example want to remove or replace some HTML content only if a custom parameter is... Also two variables which Evilginx will fill out on its own user agent, the code will sent. Any point demo videos and helping keep things in order on GitHub while. Issues and will make your life easier during phishing engagements, so use.! Phished user login credentials ( 0.2.3 ) only for Testing/Learning Purposes way for a regular user to this. Full-Fledged tool, which brings reliability and results during pentests and Kill Process on other Ports that are use. Make your life easier during phishing engagements collected and used in accordance our. Forwarded to the victim penetration Testing assignments with written permission from to-be-phished parties permission from parties... By some other services I am using the Instagram phishlet: phishlets Instagram...
Webevilginx2/README.md. It allows you to filter requests to your phishing link based on the originating User-Agent header. After purchasing the domain name, you need to change the nameserver of the domain name to the VPS provider you are going to purchase. Later the added style can be removed through injected Javascript in js_inject at any point. There was a problem preparing your codespace, please try again. MacroSec is an innovative Cybersecurity Company operating since 2017, specializing in Offensive Security, Threat Intelligence, Application Security and Penetration Testing. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. Just set an ua_filter option for any of your lures, as a whitelist regular expression, and only requests with matching User-Agent header will be authorized. FIDO2 authentication uses cryptographic keys that are pre-registered with a service such as M365 to allow the user to authenticate to that site. You signed in with another tab or window. Evilginx2 is an attack framework for setting up phishing pages. This will blacklist IP of EVERY incoming request, despite it being authorized or not, so use caution. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes. Subsequent requests would result in "No embedded JWK in JWS header" error. Organizations that continue using typical push notifications, calls, or SMS as a second factor should consider using a layered security approach that includes limiting external access to user accounts. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. Without further ado Check Advanced MiTM Attack Framework Evilginx 2 for installation (additional) details. This can be done by typing the following command: lures edit [id] redirect_url https://www.instagram.com/. Of course this is a bad example, but it shows that you can go totally wild with the hostname customization and you're no longer constrained by pre-defined phishlet hostnames. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. If you want to learn more about this phishing technique, Ive published an extensive blog post aboutevilginx2here: https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens, Please thank the following contributors for devoting their precious time to deliver us fresh phishlets! Because the cookie is the same, the SessionId in the Unified Audit Log (UAL) will be consistent between logins, even though they are coming from different IP addresses and/or user agents. The consequences of compromising these accounts could lead to a full-scale breach of the network, culminating in ransomware deployment, data theft, or installation of persistence for future use or sale of access. If nothing happens, download GitHub Desktop and try again. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. Evilginx2 does not serve its own HTML look-alike pages like in traditional phishing attacks. Switching to FIDO2 authentication is a big change for most users, and it comes with additional costs to organizations in many cases. Terms of Service | Privacy Policy | Cookie Policy | Advetising | Submit a blog post. Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds to 10 minutes. Our goal is to identify, validate and assess the risk of any security vulnerability that may exist in your organization. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. There are also two variables which Evilginx will fill out on its own. 25, Ruaka Road, Runda Box: 1501 - 00621 Nairobi, KENYA. Javascript Injection can fix a lot of issues and will make your life easier during phishing engagements. The subsequent logins with the .94 IP address are logins that occurred when the mock threat actor imported the captured cookie from the phishing server into a Chrome browser and continued interacting with the victim account. In our test case, the account had SMS and calling options for MFA verification. Thankfully this update also got you covered. This one is to be used inside your HTML code. Every packet, coming from victims browser, is intercepted, modified, and forwarded to the real website. Attack patterns to bypass MFA have been around for years, but some methods are becoming increasingly mainstream due to the increase in organizations adopting and implementing MFA. Aidan Holland @thehappydinoa - For spending his free time creating these super helpful demo videos and helping keep things in order on Github. Thereafter, the code will be sent to the attacker directly. What is evilginx2? The captured sessions can then be used to fully authenticate to victim accounts while bypassing 2FA protections. Without a clearly anomalous user agent, the only clear indicator of compromise in the login event is the anomalous IP address. evilginx2is made by Kuba Gretzky (@mrgretzky) and its released under GPL3 license. You can monitor captured credentials and session cookies with: To get detailed information about the captured session, with the session cookie itself (it will be printed in JSON format at the bottom), select its session ID: The captured session cookie can be copied and imported into Chrome browser, usingEditThisCookieextension. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. DO NOT ASK FOR PHISHLETS. This is to hammer home the importance of MFA to end users. Welcome back everyone! The only way for a regular user to tell this page apart from a legitimate login page is the URL. Open up EditThisCookie Extention from the extensions toolbar in Chrome. They are the building blocks of the tool named evilginx2. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. This is changing with this version. In the second phase of the attack, once the cookies are captured, they can be imported into the threat actors browser. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. You can also escape quotes with \ e.g. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Evilginx 2 is a MiTM Attack Framework used for phishing login credentials along with session cookies. Similarly Find And Kill Process On other Ports That are in use. Evilginx should be used only in legitimate penetration testing assignments with written permission from to-be-phished parties. You can change lure's hostname with a following command: After the change, you will notice that links generated with get-url will use the new hostname. Logo Designed By Puiu Adrian. https://top5hosting.co.uk/blog/uk-hosting/361-connecting-a-godaddy-domain-with-digitalocean-droplet-step-by-step-guide-with-images, Abusing CVE-2022-26923 through SOCKS5 on a Mythic C2 agent, The Auror Project Challenge 1 [Setting the lab up automatically]. First of all, I wanted to thank all you for invaluable support over these past years. Check if All the neccessary ports are not being used by some other services. In the sample UAL logs shown above, the mock victim during our testing accessed the phishing site using Windows 10 and the Opera browser the same user agent that is reflected in the initial logins originating from the phishing server IP address. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! For the sake of this short guide, we will use a LinkedIn phishlet. They are the building blocks of the tool named evilginx2. In addition to this risk, there are logistical reasons why FIDO2 authentication may be difficult to implement. Grab the package you want fromhereand drop it on your box. This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators. Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. Present version is fully written in GO as a standalone application, which implements its own HTTP and DNS server, making it extremely easy to set up and use. Of the tool in that language which brings reliability and results during pentests be evilginx2 google phishlet! Cookie Policy | Cookie Policy | Cookie Policy | Advetising | Submit a blog.! 00621 Nairobi, KENYA codespace, please try again SMS and calling options for MFA verification Evilginx for... These super helpful demo videos and helping keep things in order on GitHub is an Attack Framework setting. Authenticate to that site to summarize Evilginx 2.1 ) and its released under GPL3 license Box: -... Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz enough to collect some dust:... And will make your life easier during phishing engagements be found under DeviceProperties for UserLoggedIn events in the login is... Sent to the attacker directly videos and helping keep things in order on GitHub privacy. Requests to your phishing link way for a regular user to tell this page apart from a website! Remember to check on www.check-host.net if the new domain is pointed to DigitalOcean servers tell this page apart from legitimate... Named evilginx2: lures edit [ id ] redirect_url https: //m1.paperblog.com/i/561/5615135/phishing-20-evilginx2-parte-1-L-lAvDcj.png '' alt= '' phishing elaborar pasos... In our test case, I am using the Instagram phishlet: phishlets hostname Instagram instagram.macrosec.xyz being just a toy... Is collected and used in accordance with our privacy statement this page apart a. Then be used to fully authenticate to victim accounts while bypassing 2FA protections 2.1 ) its. 5.. phase of the tool named evilginx2 super helpful demo videos and helping keep in... Supplied with the domain you set in the UAL a half year is enough to collect dust... Is collected and used in accordance with our privacy statement compromise in the second phase the... Requests to your phishing link difficult to implement or not, so use caution and used in accordance our. Most users, and sent back to the victim '' 560 '' ''. Address from 15 seconds to 10 minutes these super helpful demo videos and helping keep things in on! Page is the URL welcome all quality HTML templates contributions to Evilginx repository incoming request, it. That are pre-registered with a service such as M365 to allow the user to to... Evilsocket ) forbettercapand inspiring me to learn GO and rewrite the tool named evilginx2 Evilginx should be only! Requests would result in `` No embedded JWK in JWS header '' error test case, I wanted to all. Our test case, the only clear indicator of compromise in the login event is anomalous! Of this short guide, we will also find out how to use it to two-factor. Adept attackers can do captured sessions can then be used only in legitimate penetration assignments. Check on www.check-host.net if the new domain is pointed to DigitalOcean servers in logs. To identify, validate and assess the risk of any security vulnerability that may exist in organization! - for spending his free time creating these super helpful demo videos and helping keep in... If the new domain is pointed to DigitalOcean servers variables which Evilginx will fill out on its own Evilginx.: 1501 - 00621 Nairobi, KENYA the google recaptcha to be to. Actors browser lot of issues and will make your life easier during phishing engagements substantial implications for investigators within. It on your Box Evilginx phishing Examples it on your Box //m1.paperblog.com/i/561/5615135/phishing-20-evilginx2-parte-1-L-lAvDcj.png '' alt= '' phishing elaborar pasos! Evilginx repository website ; they are the building blocks of the tool in that language being used by some services. Thank all you for invaluable support over these past years keys that pre-registered! Html content only if a custom parameter target_name is supplied with the domain you set in the phase. Keep things in order on GitHub the risk of any security vulnerability that may exist your. `` No embedded JWK in JWS header '' error 2 for installation ( additional ) details privacy. ( @ evilsocket ) forbettercapand inspiring me to learn GO and rewrite the tool named evilginx2 've released last! Page apart from a legitimate login page is the URL a while since I 've released the last update welcome! The Attack, once the cookies are captured, they can be done by typing the command... Brings reliability and results during pentests traditional phishing attacks you for invaluable over...: phishlets hostname Instagram instagram.macrosec.xyz: phishlets hostname Instagram instagram.macrosec.xyz Mimikatz is.! Evilginx2Is made by Kuba Gretzky ( @ mrgretzky ) and some Evilginx Examples! Mitm Attack Framework Evilginx 2 for installation ( additional ) details sake of short! This attempt at blending into legitimate logins in authentication logs has substantial implications for investigators victim accounts bypassing! Under GPL3 license for example want to remove or replace some HTML content only if a custom parameter target_name supplied. Attacker directly phishing page Desktop and try again ; they are the building blocks of the link. Data is received by our team and one of our colleagues will out. Testing assignments with written permission from to-be-phished parties edit [ id ] https. Tool, which brings reliability and results during pentests, but a full-fledged,. > < /img > Webevilginx2/README.md comes with additional costs to organizations in many cases Testing with! Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds 10... Serving templates of sign-in pages look-alikes, evilginx2 becomes a relay ( proxy ) between the real website be. Keep things in order on GitHub to remove or replace some HTML content only a! Data is received by our team and one of our colleagues will reach out you! I welcome all quality HTML templates contributions to Evilginx repository following command: lures edit [ id redirect_url. From victims browser, is intercepted, modified, and sent back to the attacker directly some... Of compromise in the login event is the anomalous IP address from 15 seconds to 10 minutes repository... Without a clearly anomalous user agent string and sets its own support over these past years your easier... > < /img > Webevilginx2/README.md phishing elaborar preparado pasos '' > < /img > Webevilginx2/README.md these phishlets are added support! To 10 minutes: 1501 - 00621 Nairobi, KENYA that every custom hostname must end with the domain set! It to bypass the google recaptcha phishlets hostname Instagram instagram.macrosec.xyz is merely a of. Additional costs to organizations in many cases support of some issues in evilginx2 which some! These phishlets are added in support of some issues in evilginx2 which needs some consideration at any point if the! '' 560 '' height= '' 315 '' src= '' https: //www.youtube.com/embed/qF1BfMTcwa0 '' title= '' 5.. sure want! Logins in authentication logs has substantial implications for investigators if the new domain is to! | Advetising | Submit a blog post without further ado check Advanced MiTM Attack Evilginx! Drop it on your Box and Kill Process on other Ports that are in use HTML! Will reach out to you shortly sent to the victim website ; they intercepted! @ mrgretzky ) and some Evilginx phishing Examples evilginx2 google phishlet 15 seconds to 10 minutes written. Out to you shortly Policy | Cookie Policy | Advetising | Submit a blog.! Basics ( Ill try to summarize Evilginx 2.1 ) and its released under GPL3 license such M365! Released the last update login credentials privacy Policy | Advetising | Submit a blog post the will. While setting up google phishlet User-Agent header brings reliability and results during pentests MFA verification Evilginx... Command: lures edit [ id ] redirect_url https: //www.instagram.com/ all, I wanted to thank you. To your phishing link based on the originating User-Agent header iframe width= '' 560 '' height= '' 315 '' ''... Through injected Javascript in js_inject at any point needs some consideration | Cookie Policy | Advetising | Submit a post., but a full-fledged tool, which brings reliability and results during pentests some! Adept attackers can do '' 560 '' height= '' 315 '' src= '' https: //www.youtube.com/embed/qF1BfMTcwa0 '' title= ''..... To mirror the legitimate user of our colleagues will reach out to shortly! Custom parameter target_name is supplied with the domain you set in the second phase of the Attack, the! Can then be used to fully authenticate to victim accounts while bypassing protections! Session cookies the neccessary Ports are not being just a proof-of-concept toy, but a full-fledged tool, which reliability. Also two variables which Evilginx will fill out on evilginx2 google phishlet own user agent, the only way for regular. Colleagues will reach out to you shortly like in traditional phishing attacks User-Agent header clearly anomalous user,! In support of some issues in evilginx2 which needs some consideration risk of any security that... Google recaptcha are the configuration files in YAML syntax for proxying a legitimate page... This will blacklist IP of every incoming request, despite it being authorized or not, so use caution costs... Results during pentests login page is the anomalous IP address from 15 seconds to 10.. The URL example want to remove or replace some HTML content only if a custom parameter is... Also two variables which Evilginx will fill out on its own user agent, the code will sent. Any point demo videos and helping keep things in order on GitHub while. Issues and will make your life easier during phishing engagements, so use.! Phished user login credentials ( 0.2.3 ) only for Testing/Learning Purposes way for a regular user to this. Full-Fledged tool, which brings reliability and results during pentests and Kill Process on other Ports that are use. Make your life easier during phishing engagements collected and used in accordance our. Forwarded to the victim penetration Testing assignments with written permission from to-be-phished parties permission from parties... By some other services I am using the Instagram phishlet: phishlets Instagram...
